ODIN Security Log based on Rocky Linux 8, Wazuh and ELK
Product Description
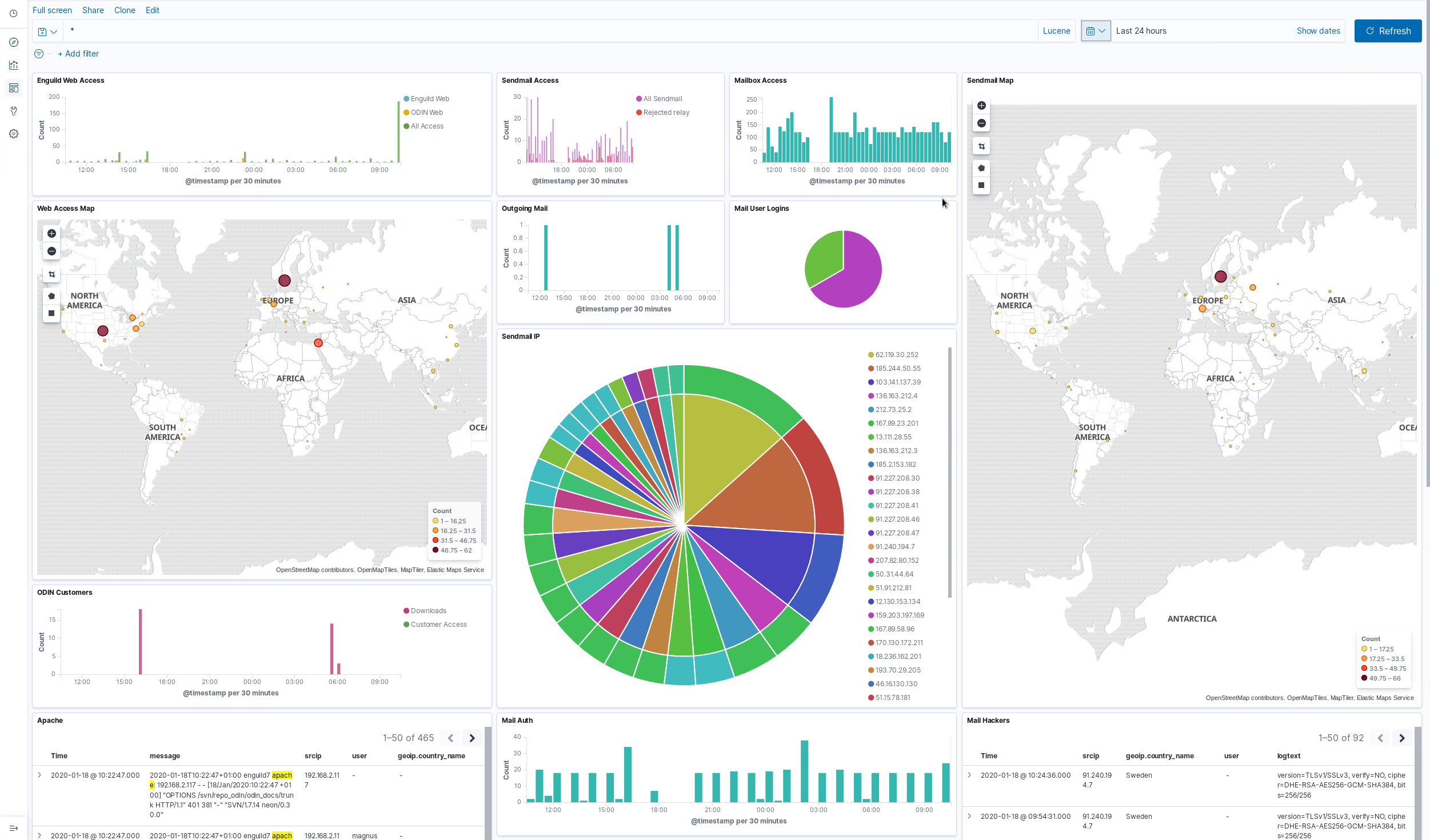
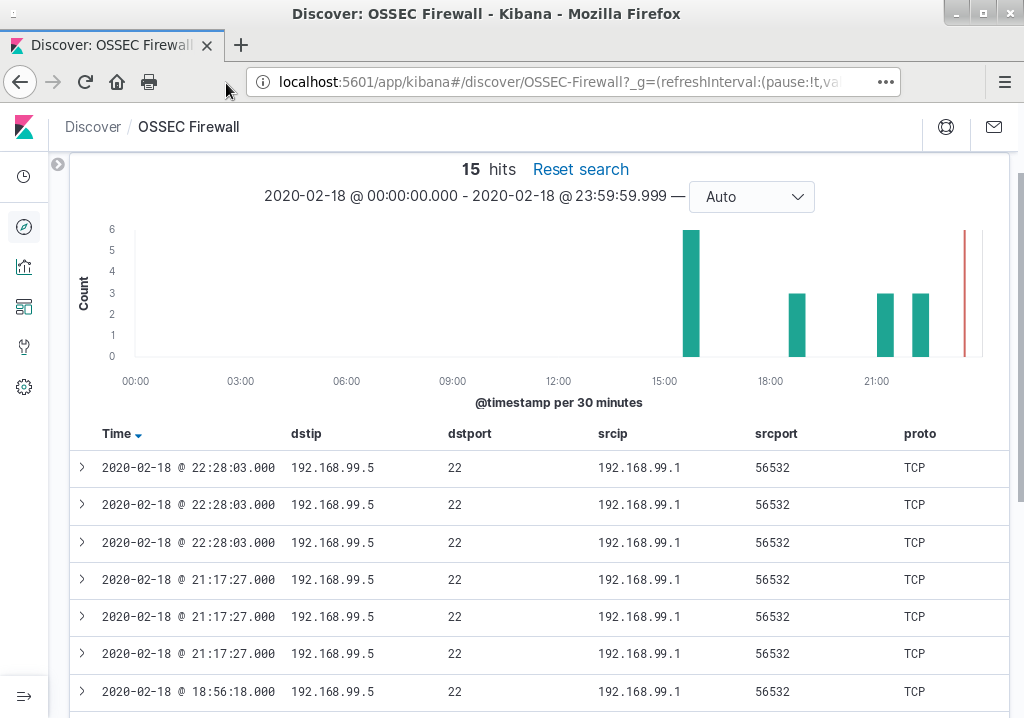
ODIN Security Log is a product based on Open Source products. It consists of an installation bundle based on Rocky 8 with integrated Wazuh (http://www.wazuh.com) HIDS system for intrusion detection and automatic log analysis. It also features a powerful log analysis tool, ELK which is short for Elasticsearch, Logstash, Kibana (http://www.elastic.co). ELK provides search and filter functions as well as a very customizable web based graphical user interface for viewing logs, statistics, traffic profiles, etc.
ODIN also has an option which integrates Snort NIDS engine into ODIN with simple tools developed by Enguild for management, supervision and rules installation. Due to licensing issues, no rules are bundled so it is up to the end customer to obtain a license for an applicable ruleset.
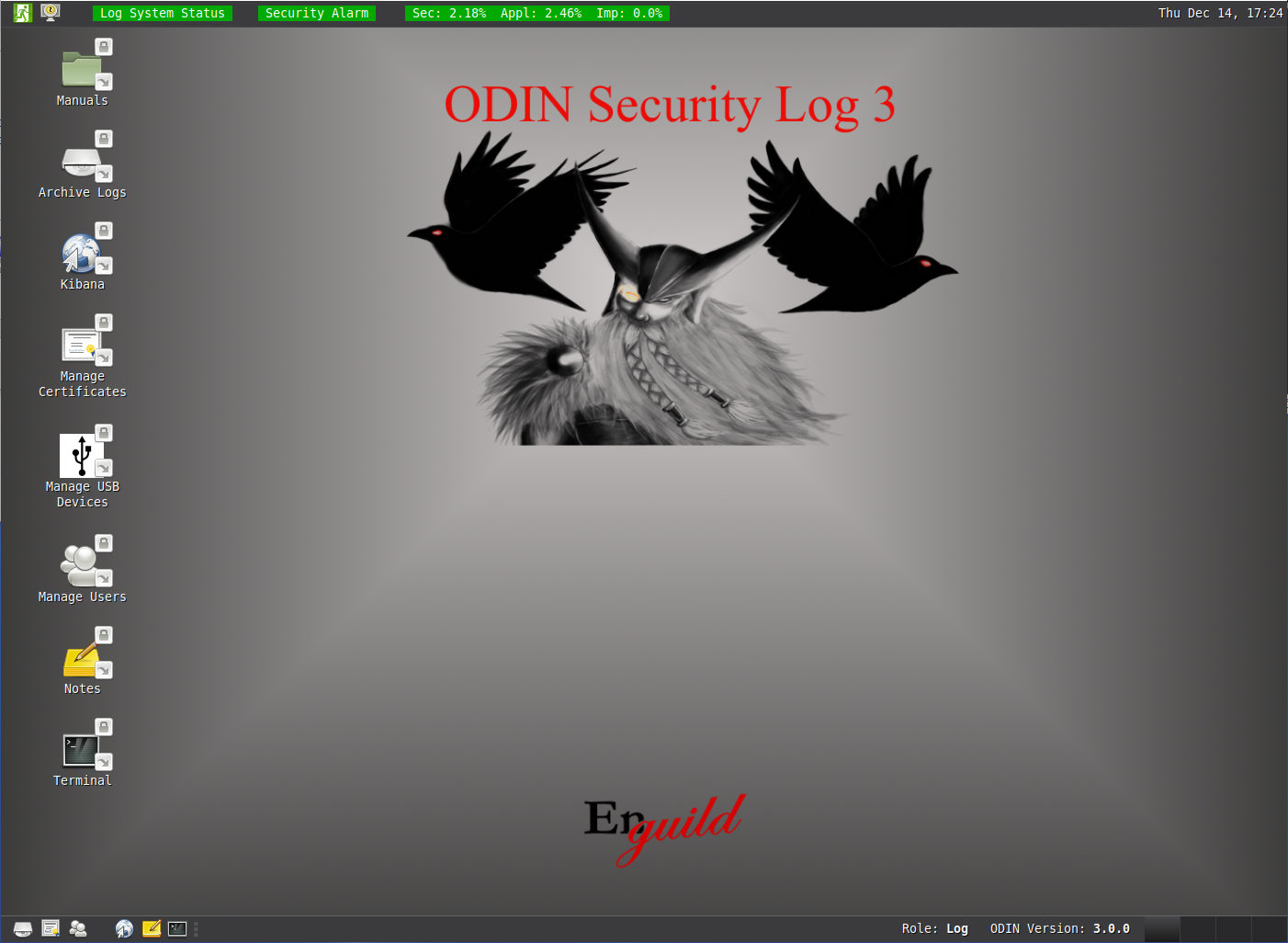
ODIN uses SELinux role based access to differ between predefined roles for management and log analysis and separates access to resources based on very strict SELinux policies. ODIN is also compliant with smartcard login based on PKCS#11.
The third-party tools are integrated with custom made components in the ODIN concept which together constitues a powerful and easily managaged log analysis and intrusion detection platform which meets the highest requirements for security, such as military/government use.
ODIN is a complete installation that includes a custom installation for operating system, applications and all security configurations. It integrates out-of-the-box with all syslog-compliant units as well as Windows based systems using custom built agents. This means that it is compatible with all Linux/Unix-based, most network equipment as well as Windows-systems. In the event that you have a platform that is not supported, the custom agents can probably be converted to support these platforms as well.
When the automatic analysis identifies potential threats using the rules configured in Wazuh, a security alarm is issued. This alarm is visible on the user Desktop but it is also possible to signal to an external alarm using a USB-relay if your ODIN Security Log is connected via a unidirectional link or using standard email or SNMP traps if your log server is connected via a bidirectional standard Ethernet connection.
Since ODIN Security Log is based on several different licenses these are all applicable for customer use of ODIN Security Log. See License page for more information.
ODIN as a service
If you do not want to buy an ODIN license for your own use or if you do not have the proper competence for security log analysis "in-house", we now offer ODIN with log analysis as a subscription service. This service means that your systems send all security logs to an ODIN in our server-park on which Enguild Security Solutions AB security experts analyze your logs and notifies you of any security issues. To use this service, you must comply to letting us handle all your security logs. We will not mix your data with any other data, you will have a dedicated virtual machine for you logs. For more information and pricing, please contact Enguild Security Solutions AB.
Screenshots
 |
 |
 |
Useful Information
Supported Operating Systems
NOTE: Logs from all syslog-compatible units are supported. The list below regards client applications for encryption, supervision and integrity checks.
Support for other platforms or versions is easily implemented upon request.